Google Cloud
Cyscale enables you to keep track and secure your Google Cloud infrastructure natively. You connect your Google Cloud project(s) by creating an IAM service account that Cyscale impersonates to read your Google Cloud resources.
Connecting Your Google Cloud Project(s)
Once you are ready to connect your Google Cloud project and have the required permissions, press the Create button from the top-right corner, select Add Connector, and choose Google Cloud. You will be greeted with a simple multi-step process.
Step 1
In the first step, you provide a name for your Google Cloud project to be used throughout Cyscale. This is a plain-text identifier that helps you better manage your resources.
You also provide the project ID. You get this information from your Google Cloud Console (Cyscale will show you precisely how).
Step 2
In the second step, you create the service account that Cyscale will use to read your infrastructure. The output of this step is a JSON file with the service account's credentials.
Terraform (Default)
Based on the project ID you provided in the first step, Cyscale generates a ready-to-use Terraform configuration file. You download this file and, using the Terraform CLI either from your machine or using Cloud Shell, you create the service account, assign the required roles, and create the key.
Terraform uses the provider's APIs/SDKs to manage the resources. The Terraform Google Cloud provider can be configured in several ways which you can find here.
We recommend using user application default credentials that you can create with the command gcloud auth application-default login (in case you are running the command from WSL, you might want to add the argument --no-launch-browser)
Inspect the Terraform configuration file, run terraform init and terraform apply -auto-approve. Terraform creates the service account, assigns the required roles, creates the key, and outputs the credentials. Since the key is sensitive information, you have to output it in a file using the command terraform output -raw credentials_key > gcp-key.json (the name of the file is not important). Upload this file to Cyscale. You will see something like
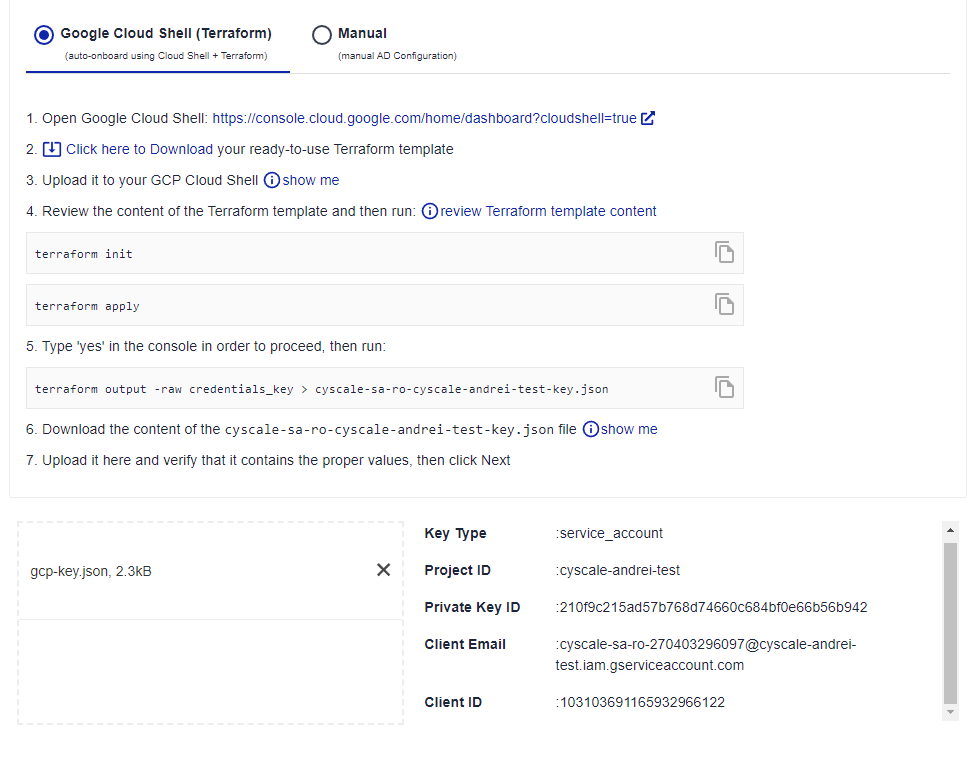
Besides being simple to use, it provides a great way to manage the lifecycle of the created resources. For example, if you decide to remove the connection to your Google Cloud project, you simply run terraform destroy to delete all Cyscale-related resources from your project.
Manual
If you prefer setting up the resources manually from the Google Cloud Console, follow the steps described in the application. You can also find the steps for creating a service account in the Google Cloud documentation.
While the permissions you grant to Cyscale are limited to reading the configuration of your cloud resources, you might still be concerned about the security of your Google Cloud project. Providing the service account key to Cyscale means that any entity with access to the key can read your Google Cloud resources.
Cyscale encrypts and stores the credentials in a database accessible only from within the Cyscale infrastructure. Then, a specialized microservice decrypts and uses the credentials to sync your Google Cloud assets. No member of the Cyscale team has access to your credentials.
Step 3
In the third step, the system makes sure the connection to your cloud account can be established and starts the first sync in the background. You can navigate to the cloud account overview page. The page will automatically refresh when the sync and assessment are completed.
Certain resources such as IAM resources (users, service accounts, etc.) do not belong to a certain region. These are classified by Cyscale as global assets.
Deep Dive on Permissions
Roles
The permissions Cyscale has with regards to your Google Cloud infrastructure are dictated by the roles you assign to the service account you create in step 2.
To benefit from everything Cyscale has to offer, the following roles are needed:
- Viewer - This is a built-in basic role that allows read access to most resources in the project. You can read more about the Viewer role in the Google Cloud documentation, and you can see all permissions granted through this role with the command
gcloud iam roles describe roles/viewer. - Security Reviewer - Built-in role allowing read access to all resources. It is required because some key
listpermissions are not granted by the viewer role. You can read more about this role and see all the permissions that it grants in the Google Cloud documentation. - Cloud Asset Viewer - Built-in role allowing read access to Cloud Asset Inventory. Cyscale only needs this to read images stored in Google Container Registry (GCR) (there is no other way/API to read them). If you are not storing container/docker images on Google Cloud or you are using Artifact Registry, you don't need to provide this role.
It is important to make the distinction between infrastructure/configuration access and data access. Since Cyscale focuses currently on infrastructure, these roles do not grant permissions to your data. For example, Cyscale can read the configuration of your Cloud Storage buckets, but not their actual content (the objects) - i.e. there are no storage.objects.* permissions.
Service APIs
In order to use most services from Google Cloud, you have to enable the APIs of the respective services. For example, to create a VM, you will have to enable the Compute Engine API. Cyscale does not require you to enable APIs that you do not use. You can read more about service APIs in the Google Cloud documentation.
Managing Your Connected Google Cloud Project(s)
Once connected, your Google Cloud project(s) will show up in the Connectors list. From there, you can either use the inline actions or navigate to the overview page of the cloud account. The available options are:
Configure
You can update the following information for your Google Cloud cloud accounts:
- Name - this helps you better identify the cloud account throughout the Cyscale platform
- Project ID
- Service account key - by default in Google Cloud, the service account key does not expire. However, you might want to rotate it or create another service account.
Disable/Enable
By default, all connectors are enabled. If you want to prevent Cyscale from syncing and assessing your assets for a certain connector, you can disable it. The state of the connector in Cyscale will be locked until you enable it again. The assets will not be updated based on your actual resources and assessments will not be performed for them.
Sync
You can always trigger a new sync and assessment manually for a given connector (unless the sync is already in progress). This will make Cyscale read all your resources for that particular connector, evaluate the applicable controls, and generate any alerts if necessary.
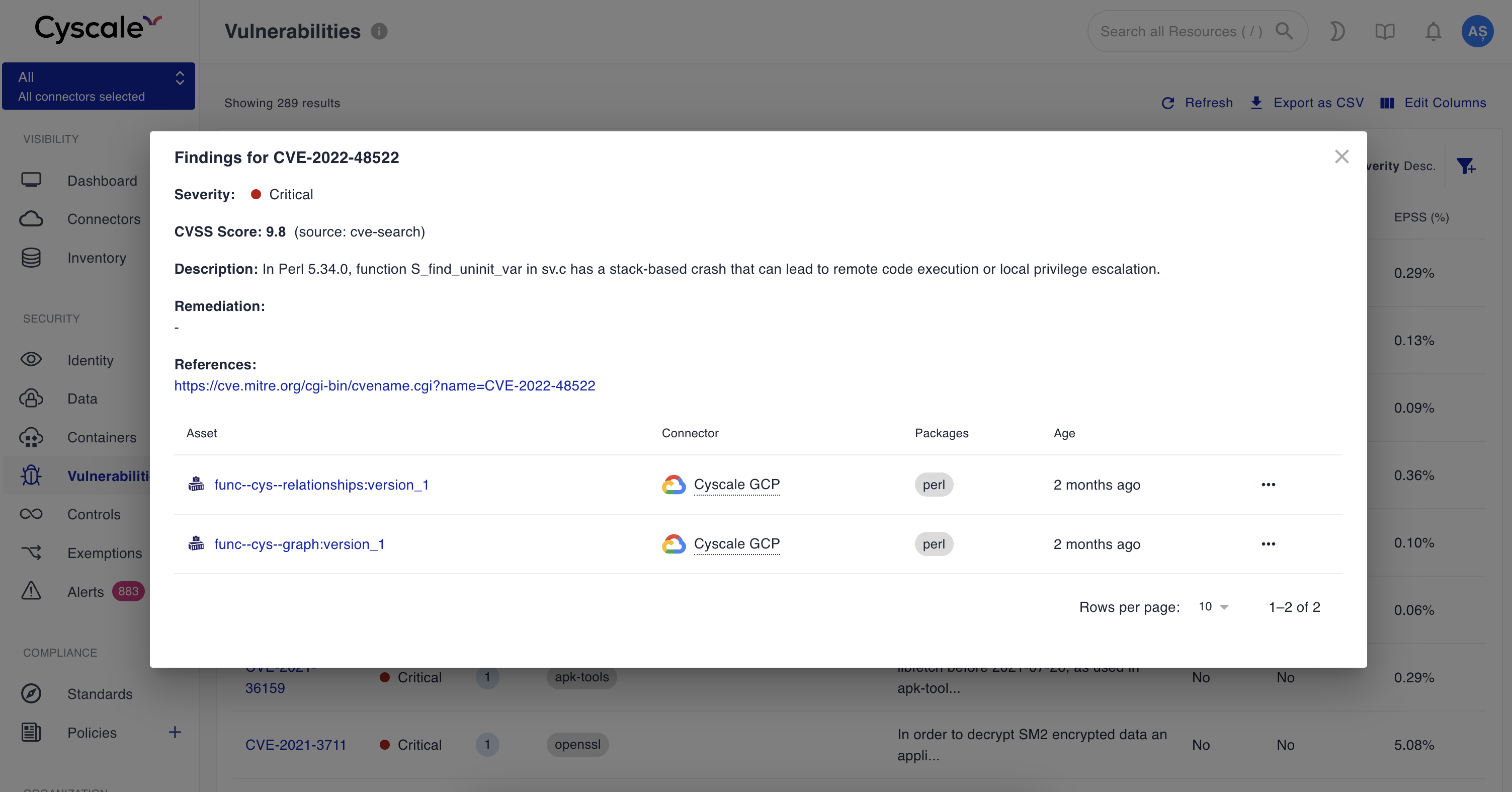
Vulnerabilities
If you are using the OS scanning feature of Artifact Registry, Cyscale will automatically pull the reported vulnerability findings, enrich them from other sources, and display the findings in the context of your infrastructure (e.g. on the Cloud Run services running the vulnerable images):
Service Coverage
The Google Cloud resources that Cyscale can handle are listed in the tables below, along with the number of controls that check their configuration:
| Compute | # of Controls |
|---|---|
| Cluster | 18 |
| Function | 1 |
| VM | 8 |
| Databases | # of Controls |
|---|---|
| BigQueryTable | 1 |
| BigTable | 0 |
| CloudSpanner | 0 |
| CloudSQLInstance | 18 |
| IAM | # of Controls |
|---|---|
| IAMGroup | 0 |
| IAMPermission | 0 |
| IAMPolicy | 0 |
| IAMRole | 1 |
| IAMServiceAccount | 4 |
| IAMServiceAccountKey | 1 |
| IAMUser | 5 |
| Integration | # of Controls |
|---|---|
| PubSubLiteSubscription | 0 |
| PubSubLiteTopic | 0 |
| PubSubSubscription | 1 |
| PubSubTopic | 1 |
| Management | # of Controls |
|---|---|
| CloudAccount | 10 |
| Project | 1 |
| Networking | # of Controls |
|---|---|
| Firewall | 10 |
| ManagedZone | 3 |
| NetworkInterface | 0 |
| PublicIP | 0 |
| Subnetwork | 0 |
| TargetHTTPSProxy | 1 |
| TargetSSLProxy | 1 |
| VPC | 4 |
| Operations | # of Controls |
|---|---|
| AlertPolicy | 0 |
| LogBucket | 1 |
| LogMetric | 0 |
| LogSink | 0 |
| Security | # of Controls |
|---|---|
| KMSKey | 9 |
| SSLPolicy | 0 |
| Storage | # of Controls |
|---|---|
| Bucket | 12 |
| Disk | 2 |